1. Browse to https://github.com/sophos-iaas/xg-azure and select Deploy to Azure. This will open up the custom deployment template in Azure. 
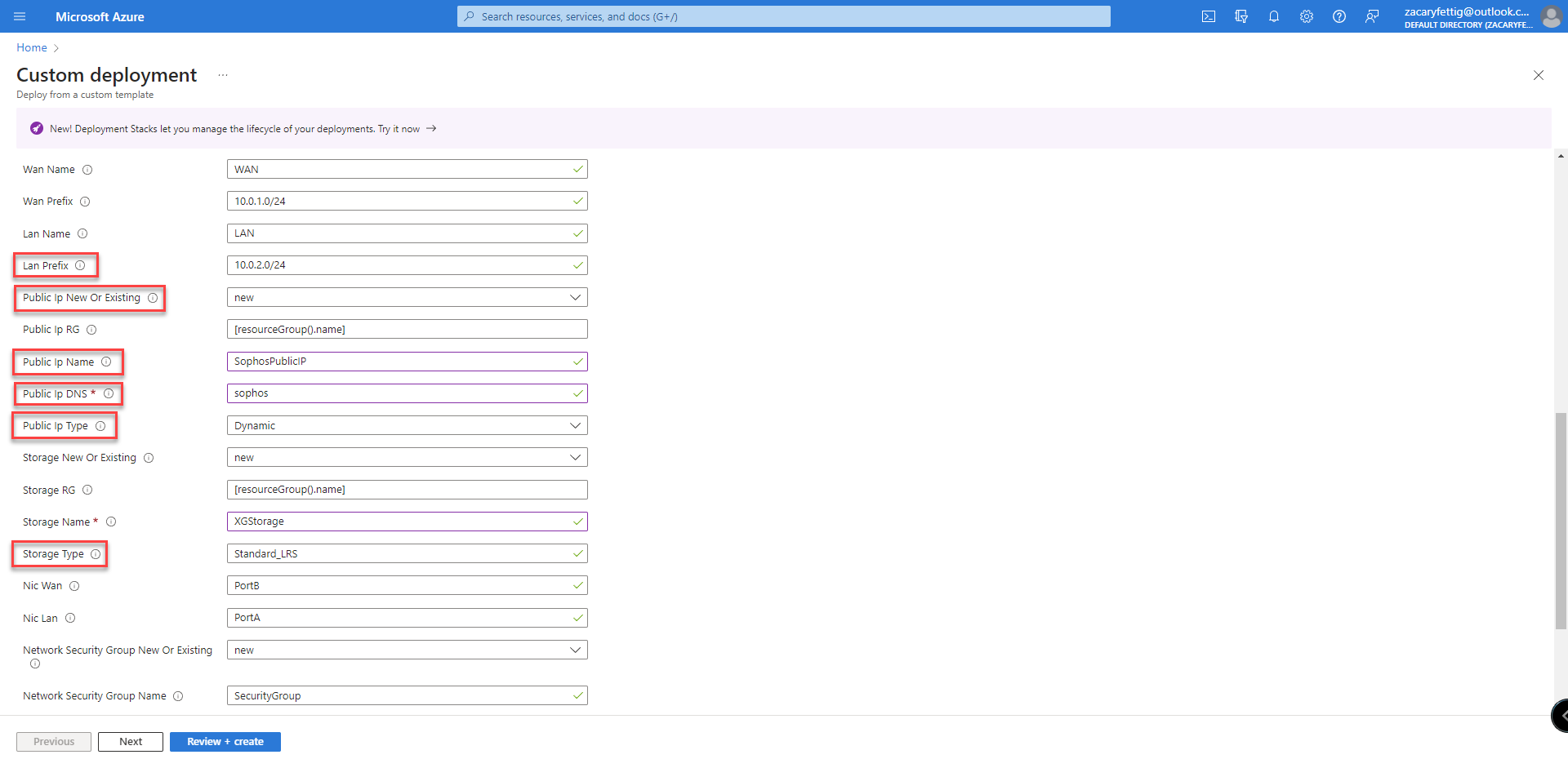
2. Custom template opens in Azure. Select resource group, region, vm name, admin password, image sku (byol/pay-as-you-go), lan prefix for adjusting lan subnet, public IP name, publicIP DNS prefix name, Dynamic assigned or statically set, storage account redundancy. Trusted network defines where the Sophos Administration Portal can be accessed from. The last setting sets the number of instances of firewalls to be deployed. Select review + create.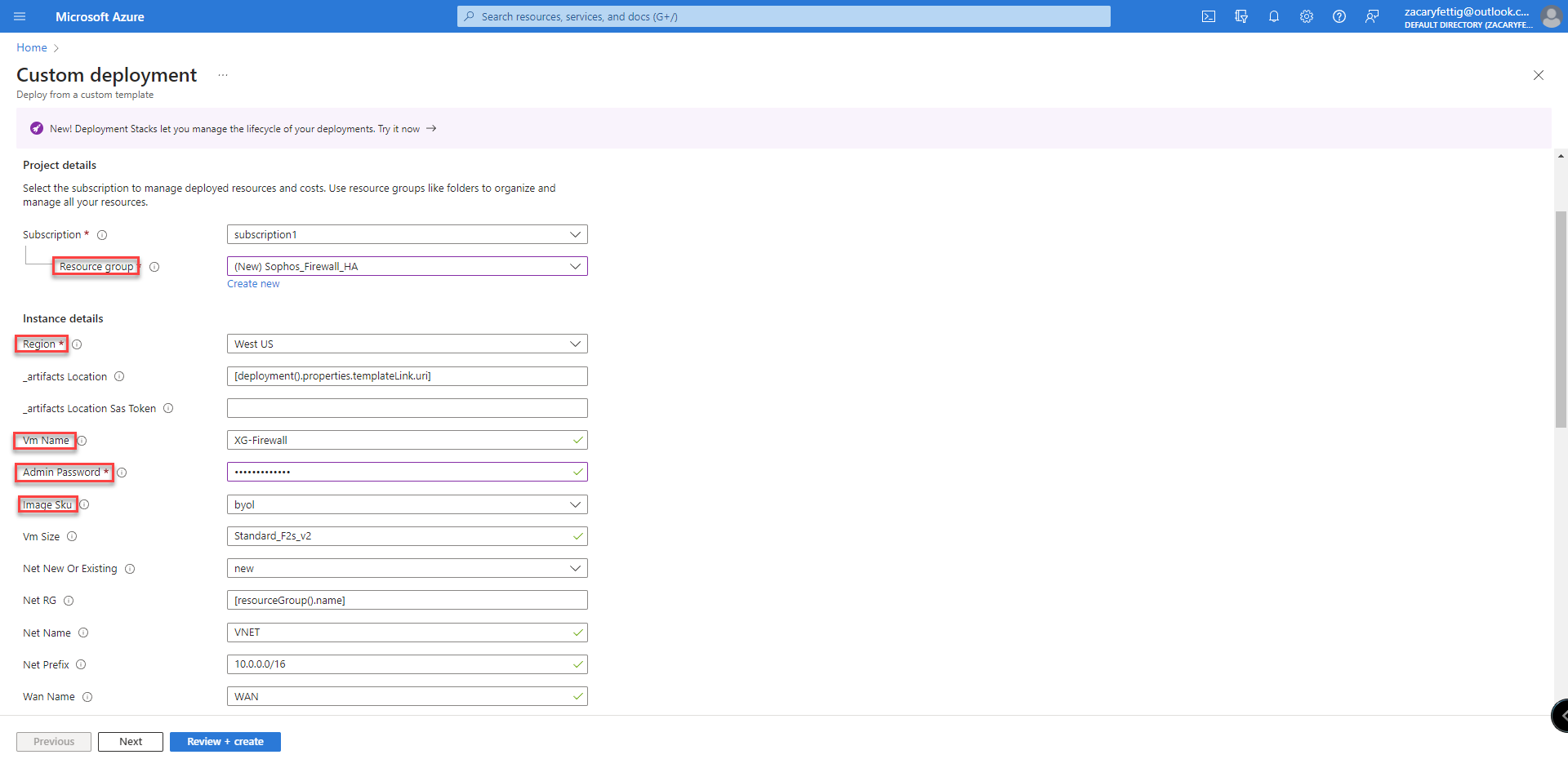

3. Ge the public IP address of the first firewall by going to the Public Pp Address Resource in Azure and viewing the Public IP from the overview section.
4. Use port 4444 to connect to the Sophos XG Admin Portal. Ex. https://51.143.123.14:4444
5. At the next screen after sign in, register your Firewall with Sophos, in order to pull down licensing. 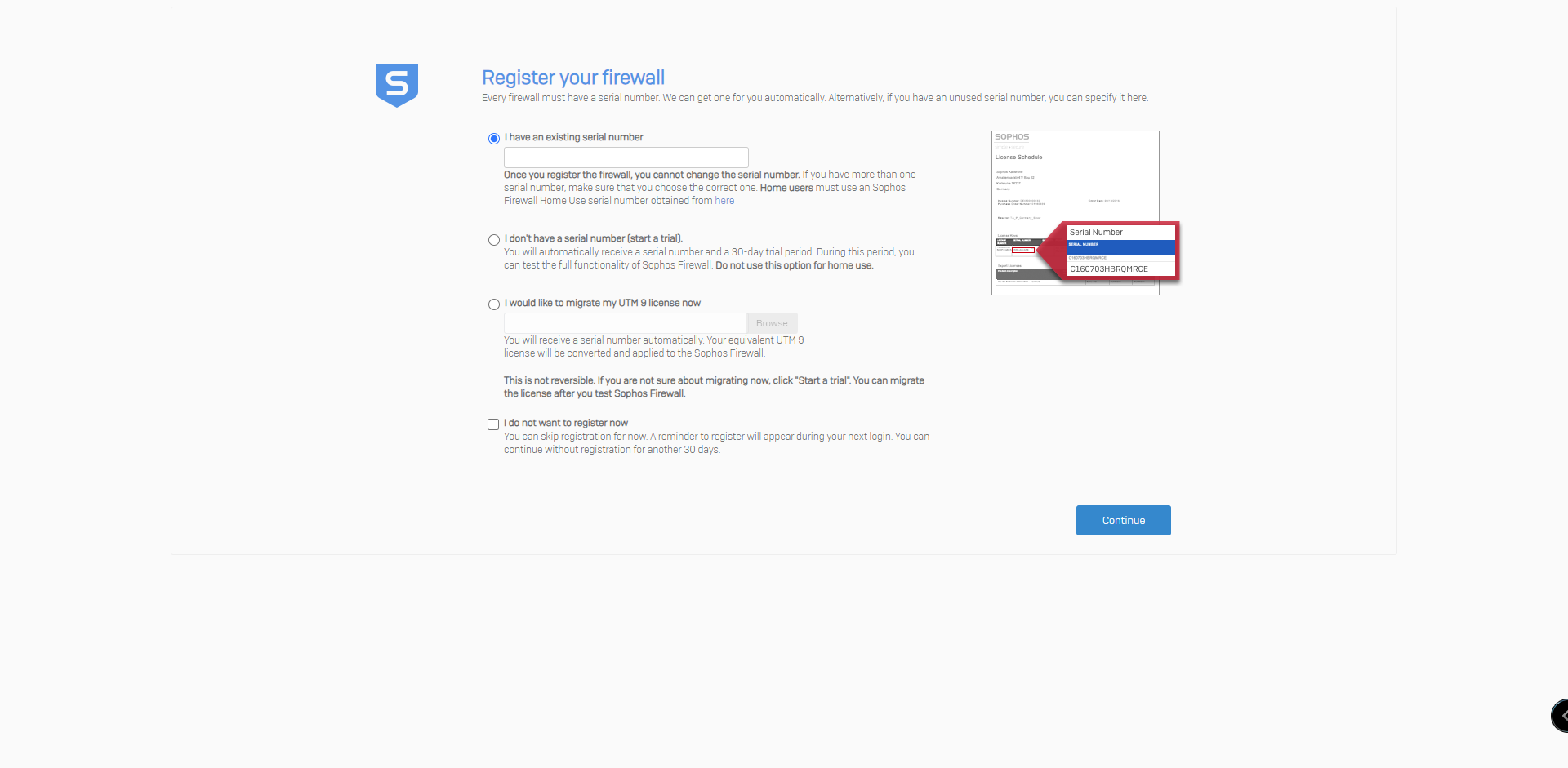
6. After wizard has completed, select create Secure Storage Master Key. The Storage Master Key will be used as an extra protection that is required for creating backups. 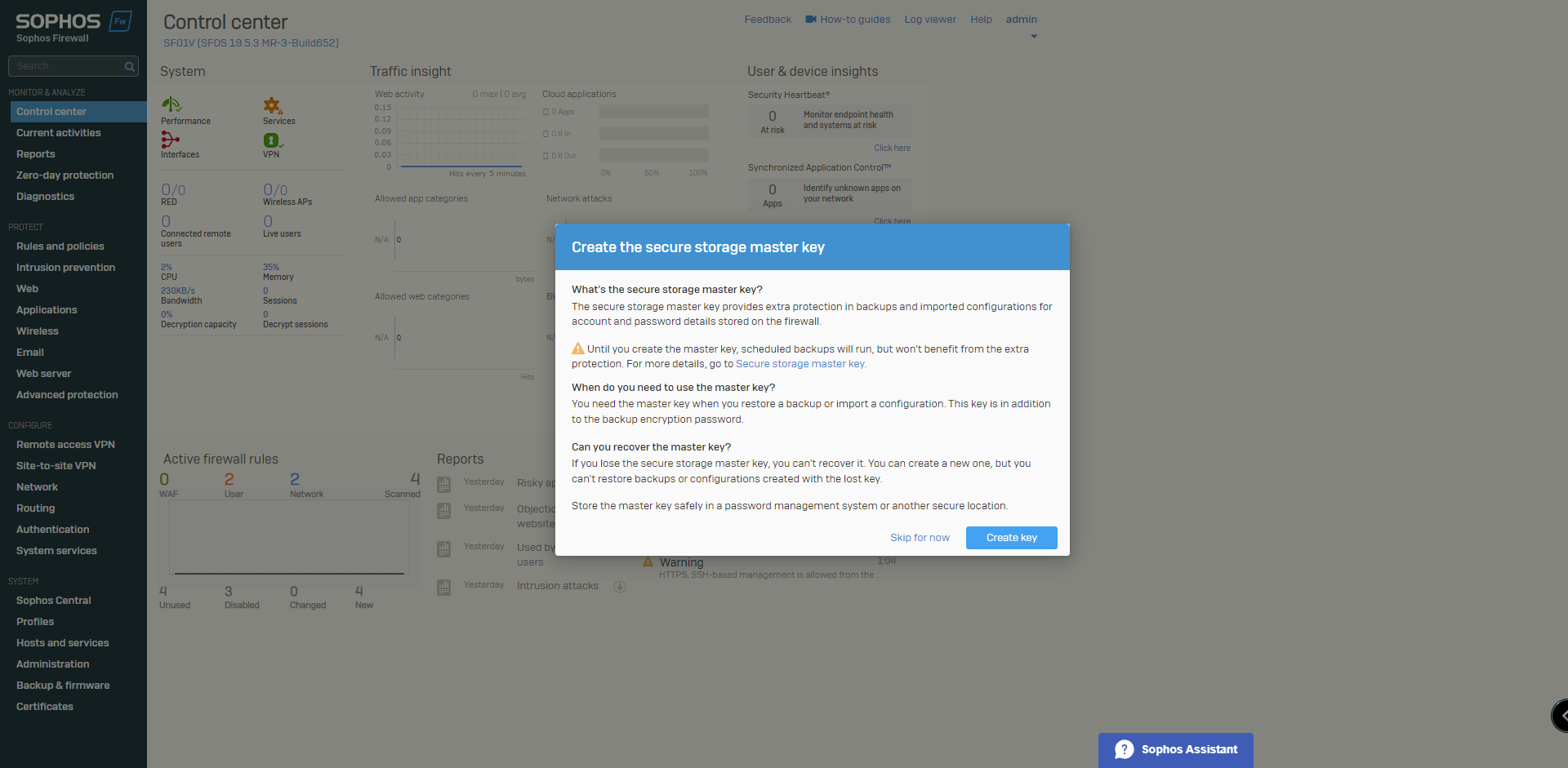
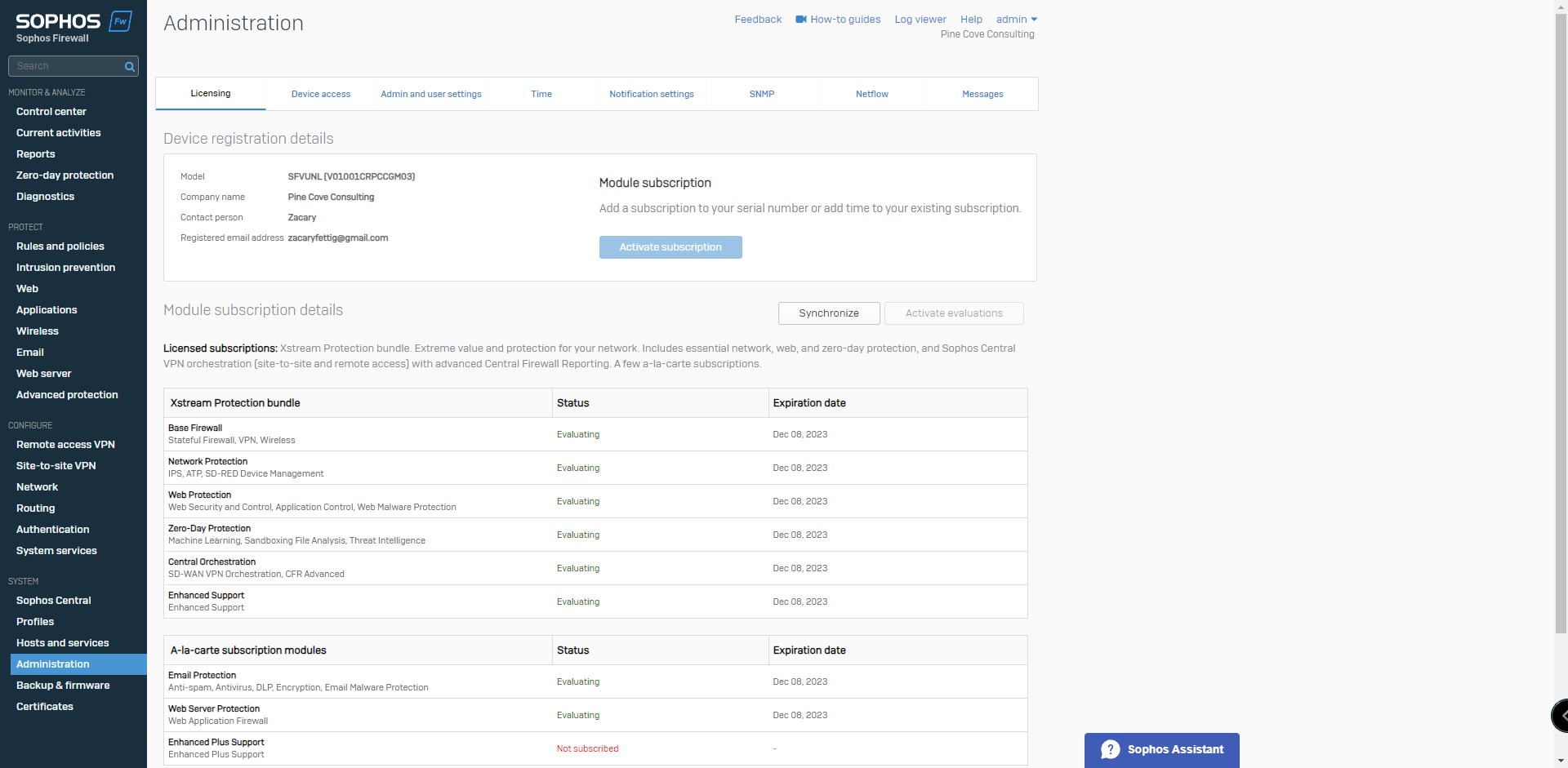
7. Sophos Central Registration enables the firewall to be accessed and configured from your Central Cloud Account. On the Sophos Central tab under the system section, select Register. 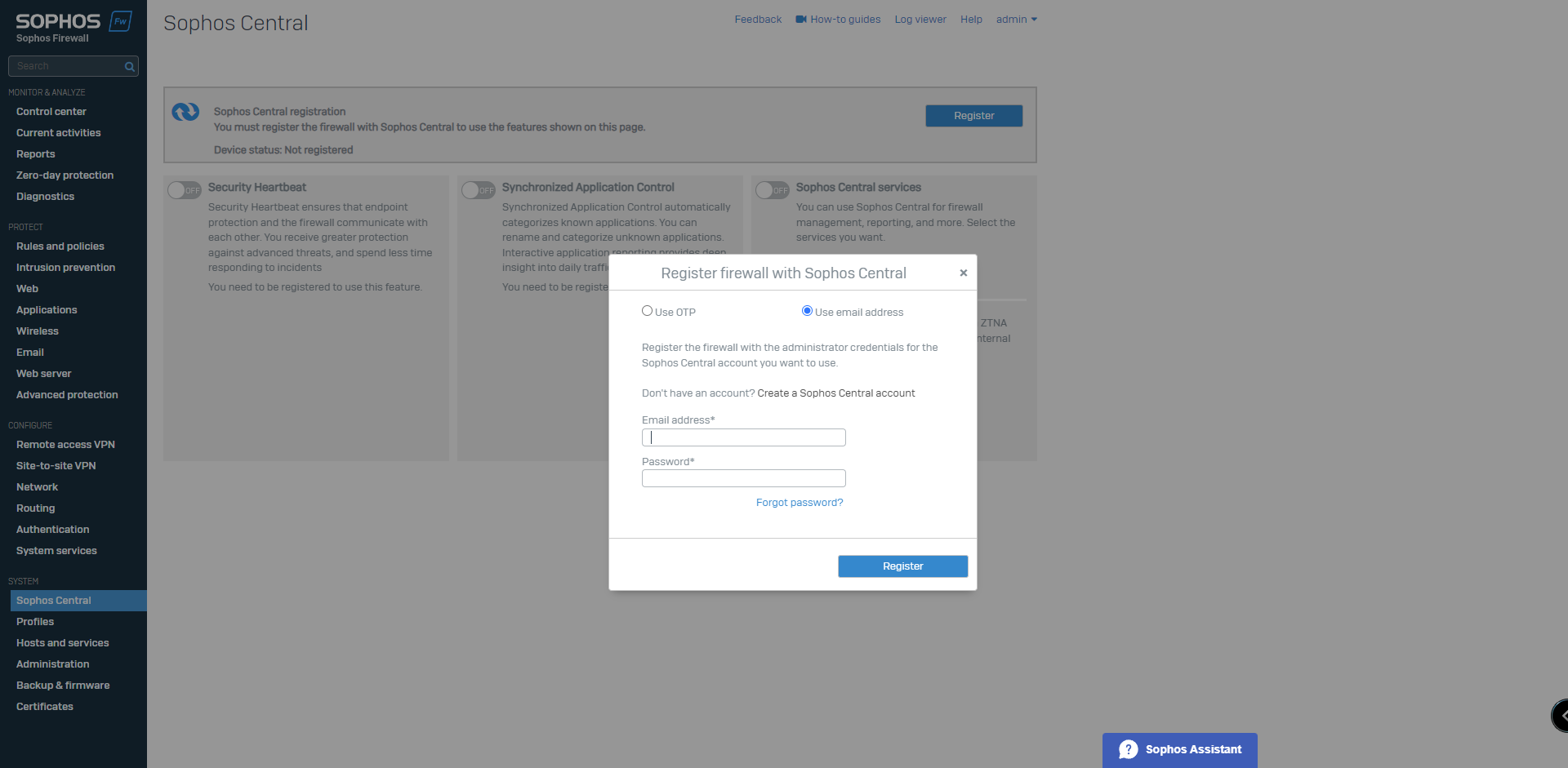
8. Enable to toggles and the check boxes when enabling Sophos Central Services toggle.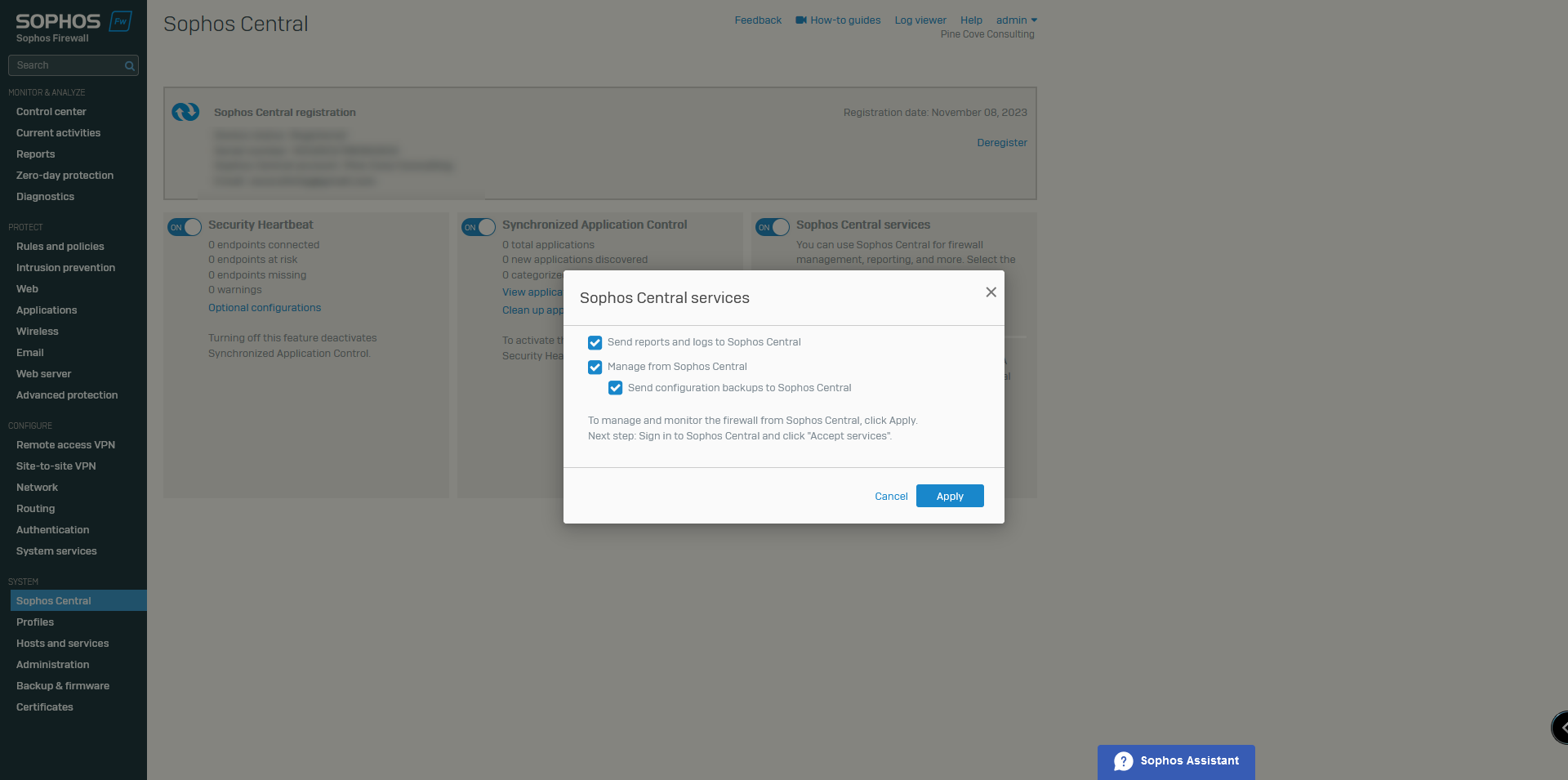
9. Connect to the same public IP with port 4445 to access the second firewall. Repeat the same steps on the second firewall. 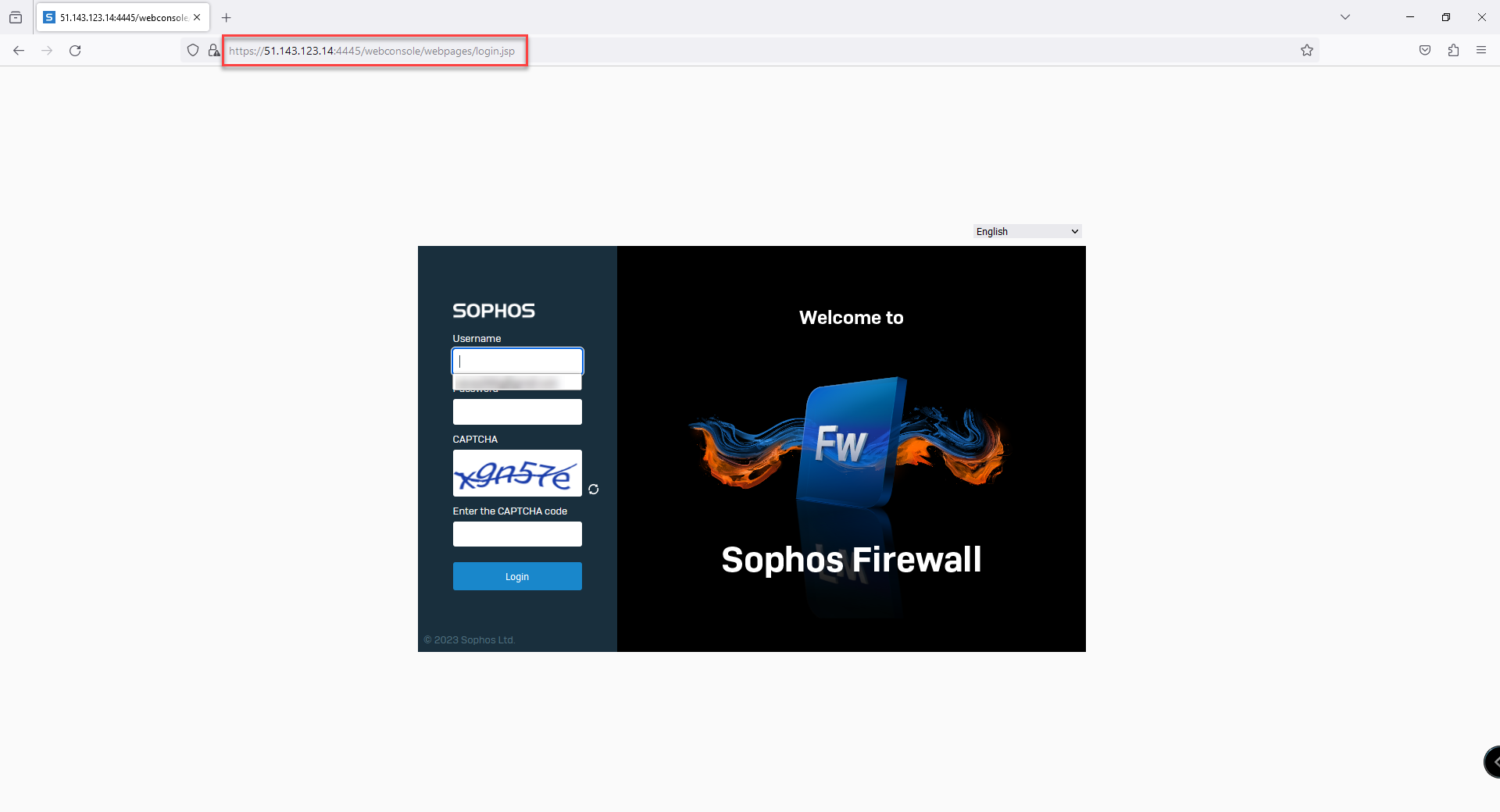
10. Firewalls will appear in central. Create a group using the Create New Group button on the top right. Add firewalls to the group by selecting edit group.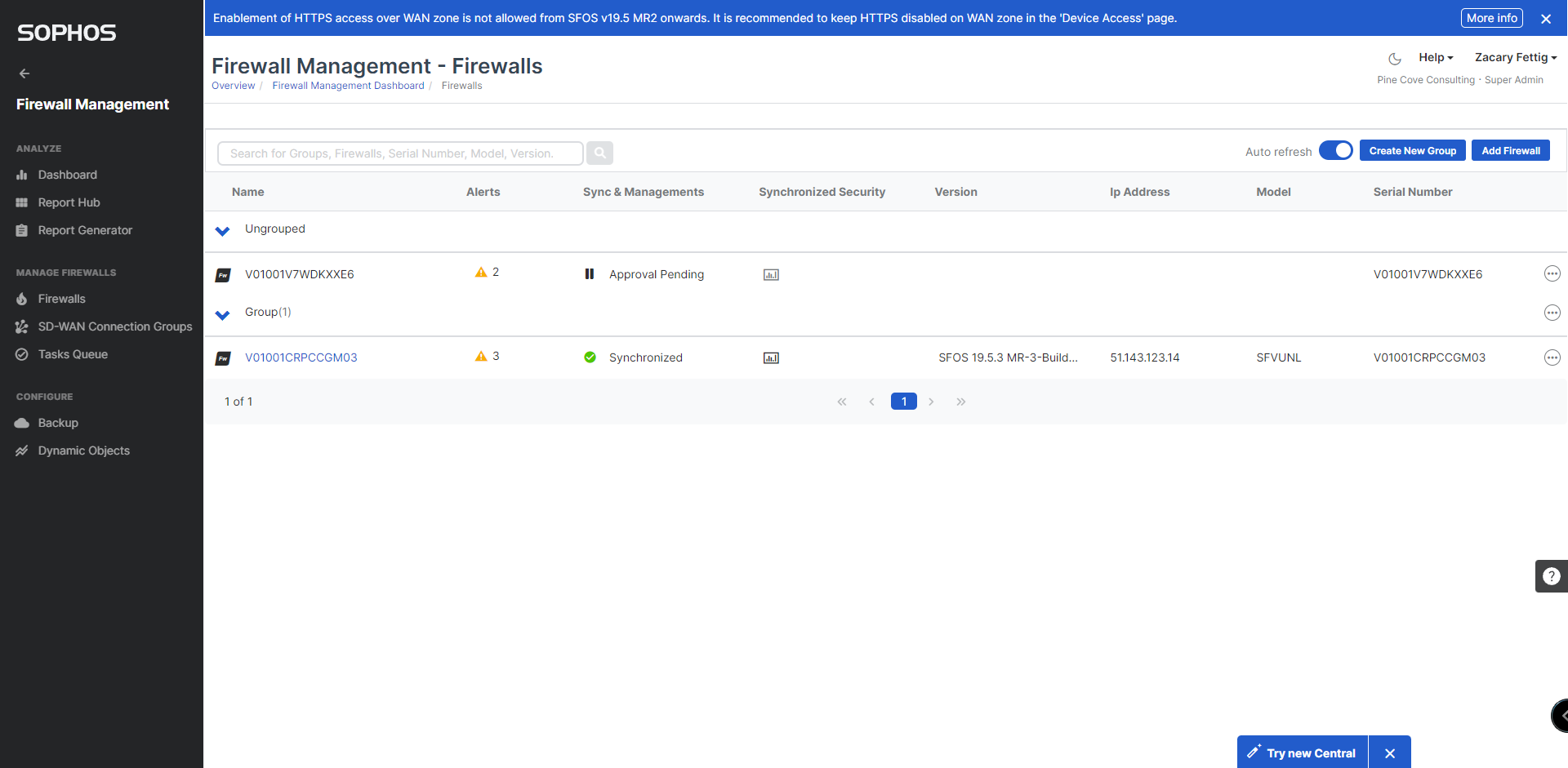
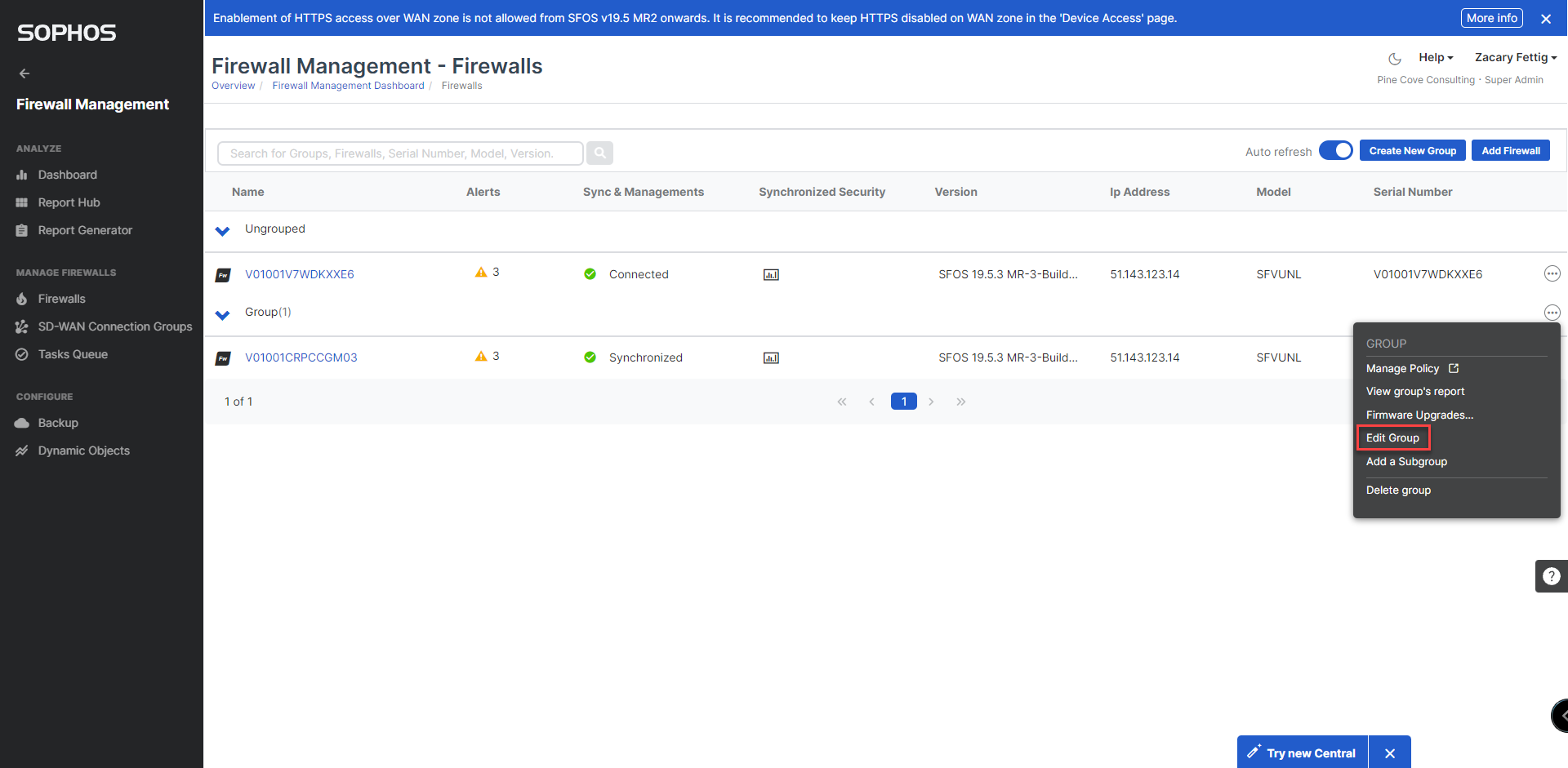
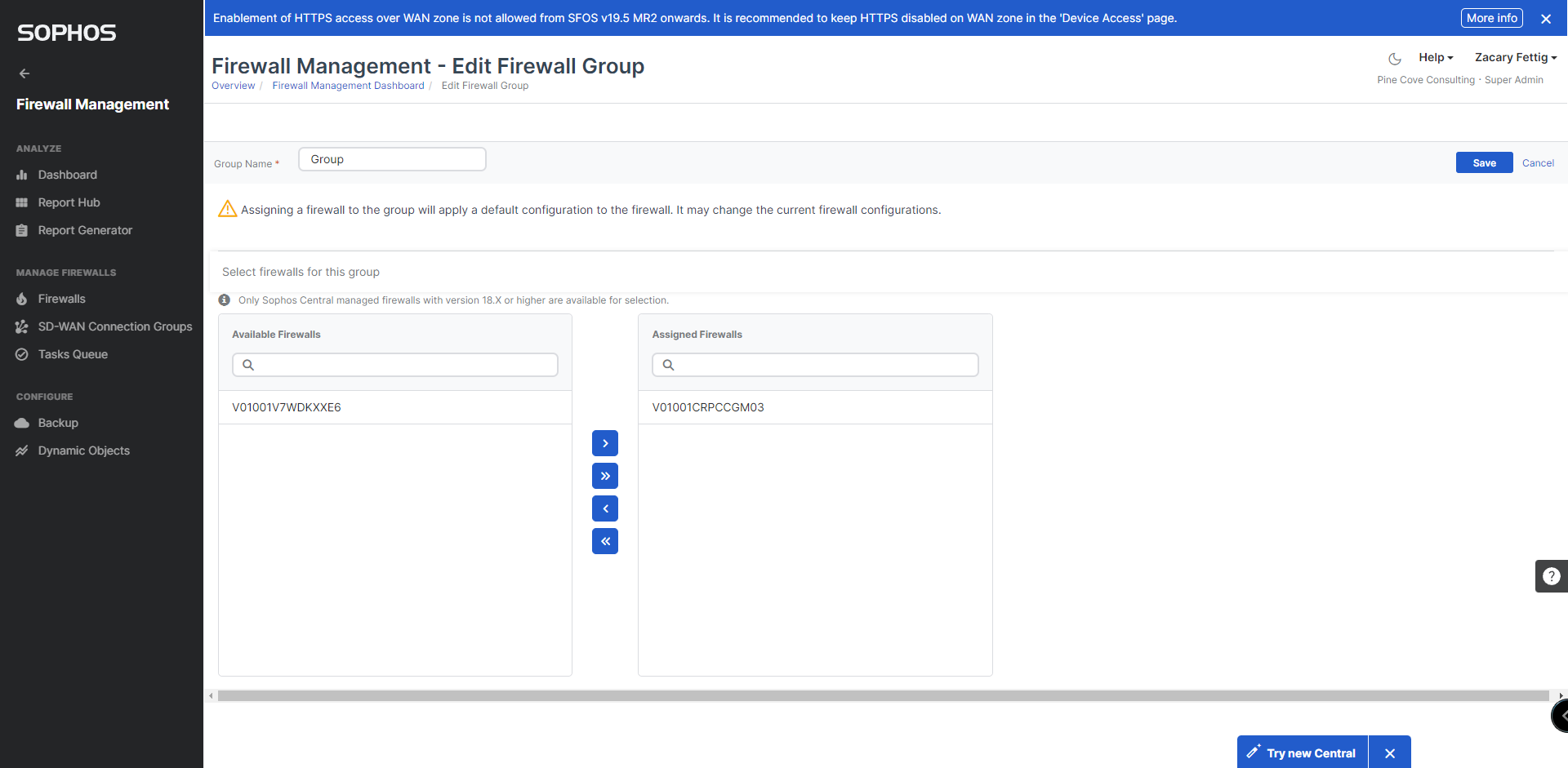
11. Select manage policy from the menu.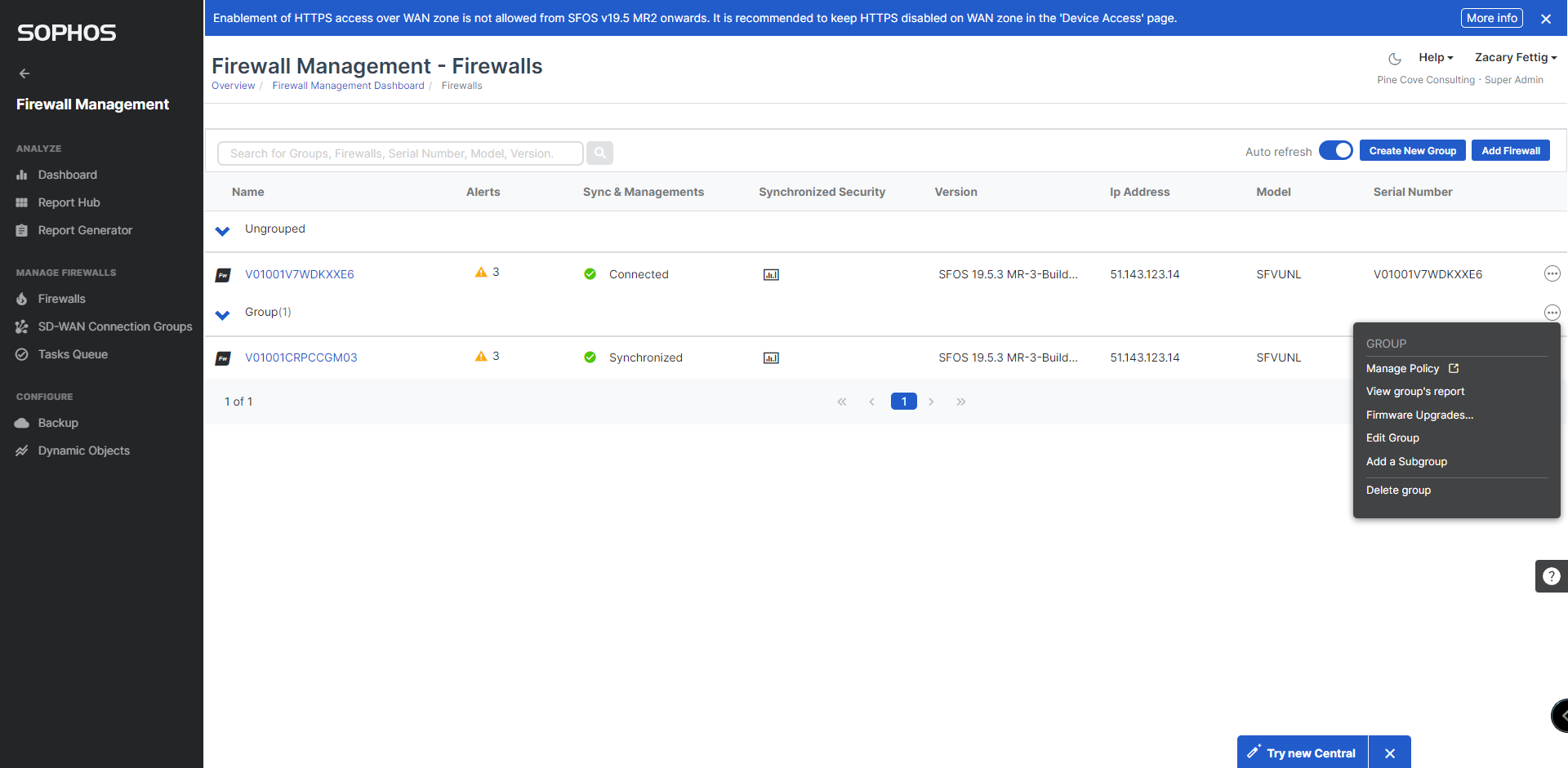
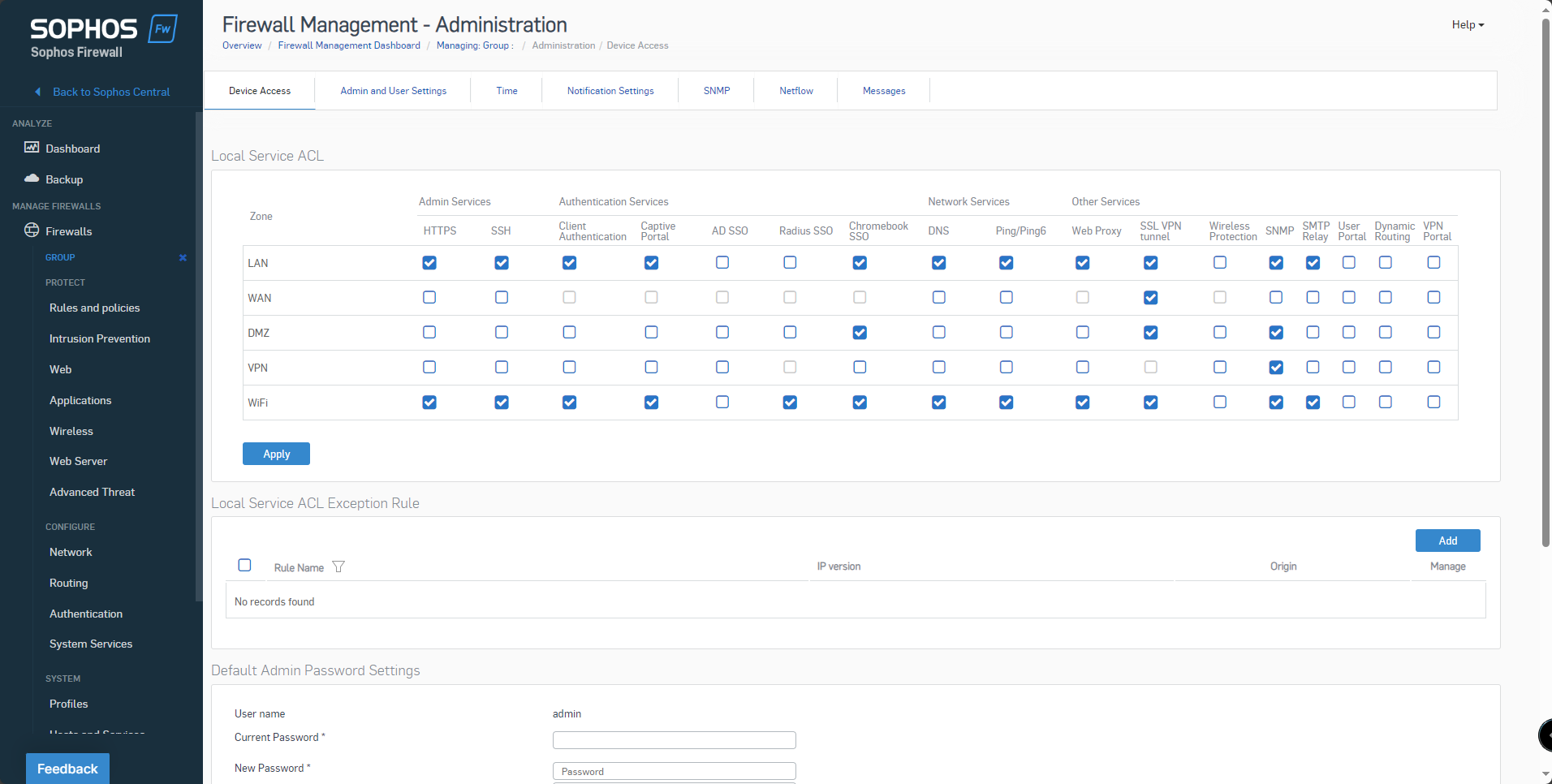
12. Policy Manager can manage Firewall Rules, Nat Rules, and firewall settings for the HA pair.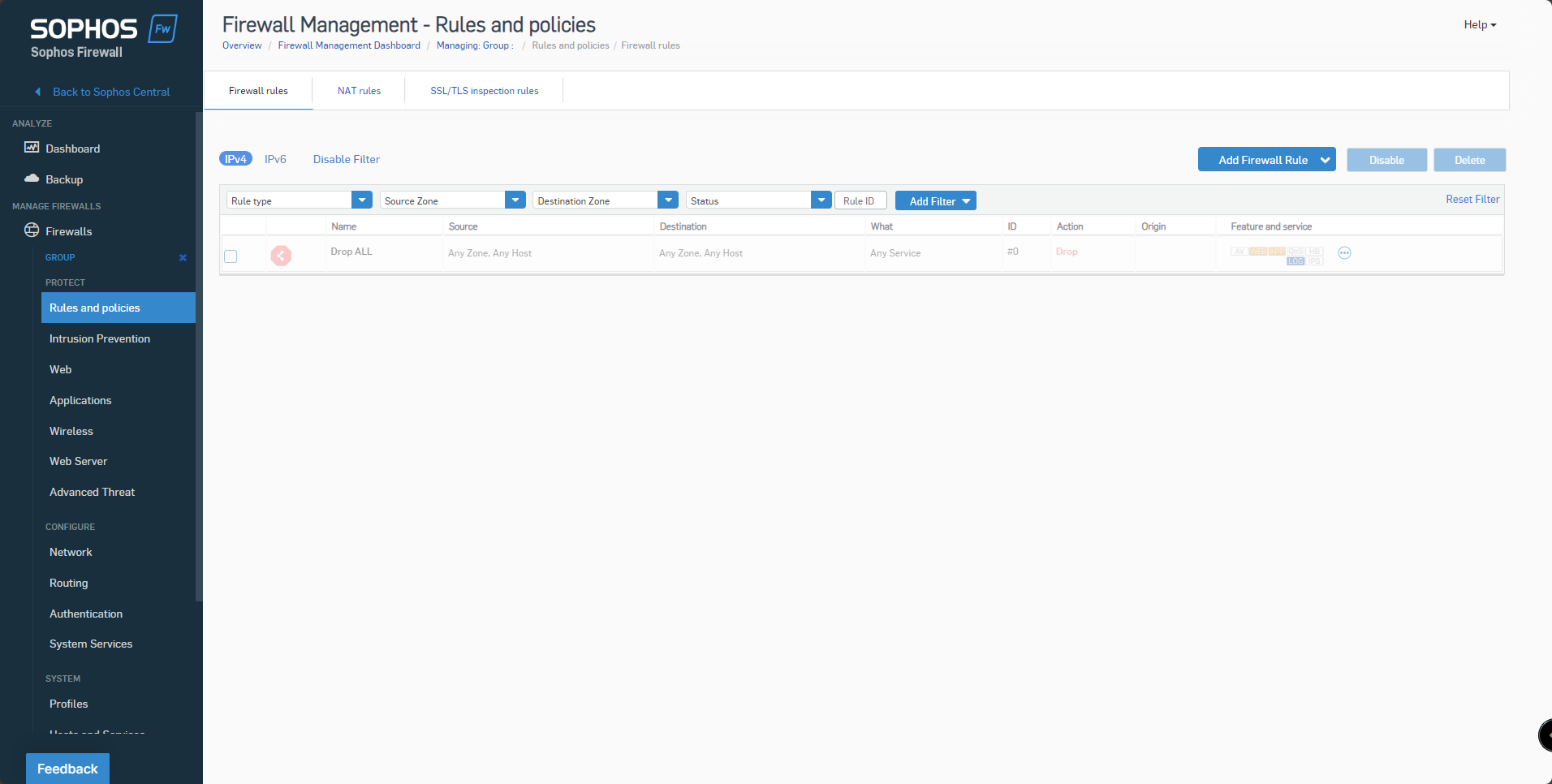
Sophos has created a detail detailing Multi Node Management from Sophos Central. https://www.youtube.com/watch?v=I4heqD2NpJ8
In this lab, I created an additional subnet to be used as the servers subnet. Steps below detail how to connect that subnet back to the XG.
1. Create a new subnet in the subnets section of the LAN side vnet.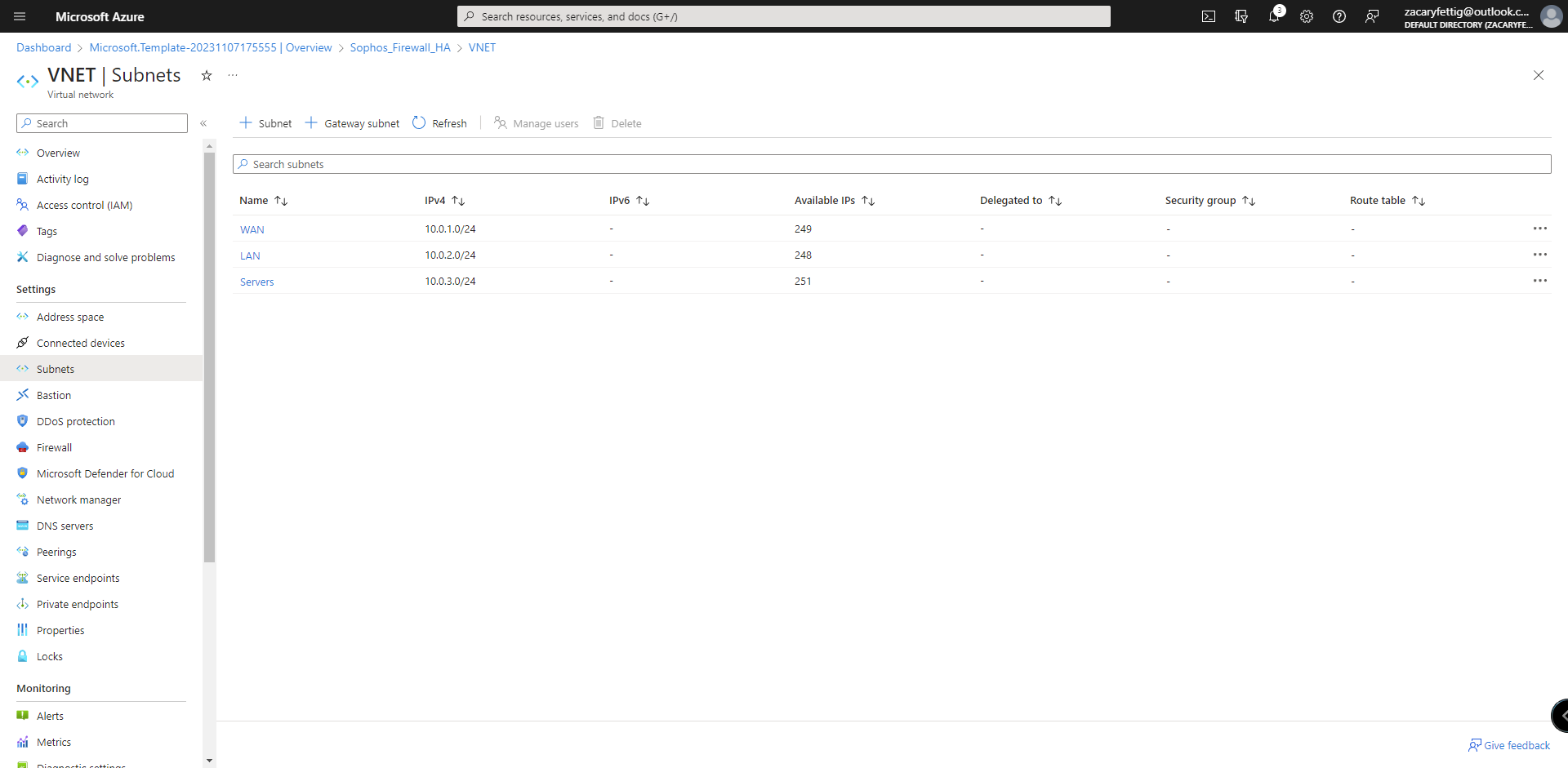
2. Add Route table and assign it to the subnet to route traffic back to the XG.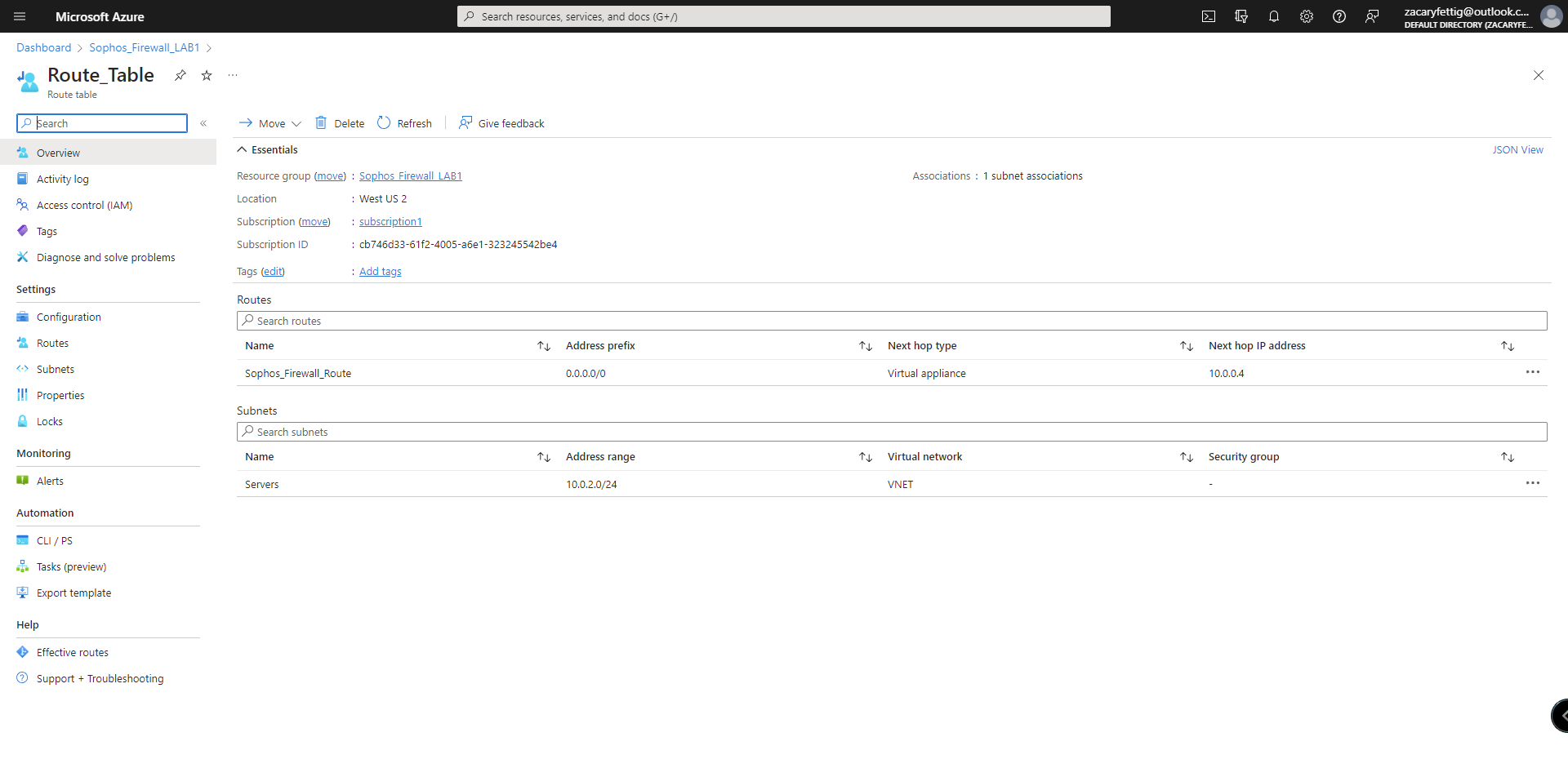
3. Create a new route. Destination IP is all traffic in the subnet. Next hop address is the internal port A load balancer.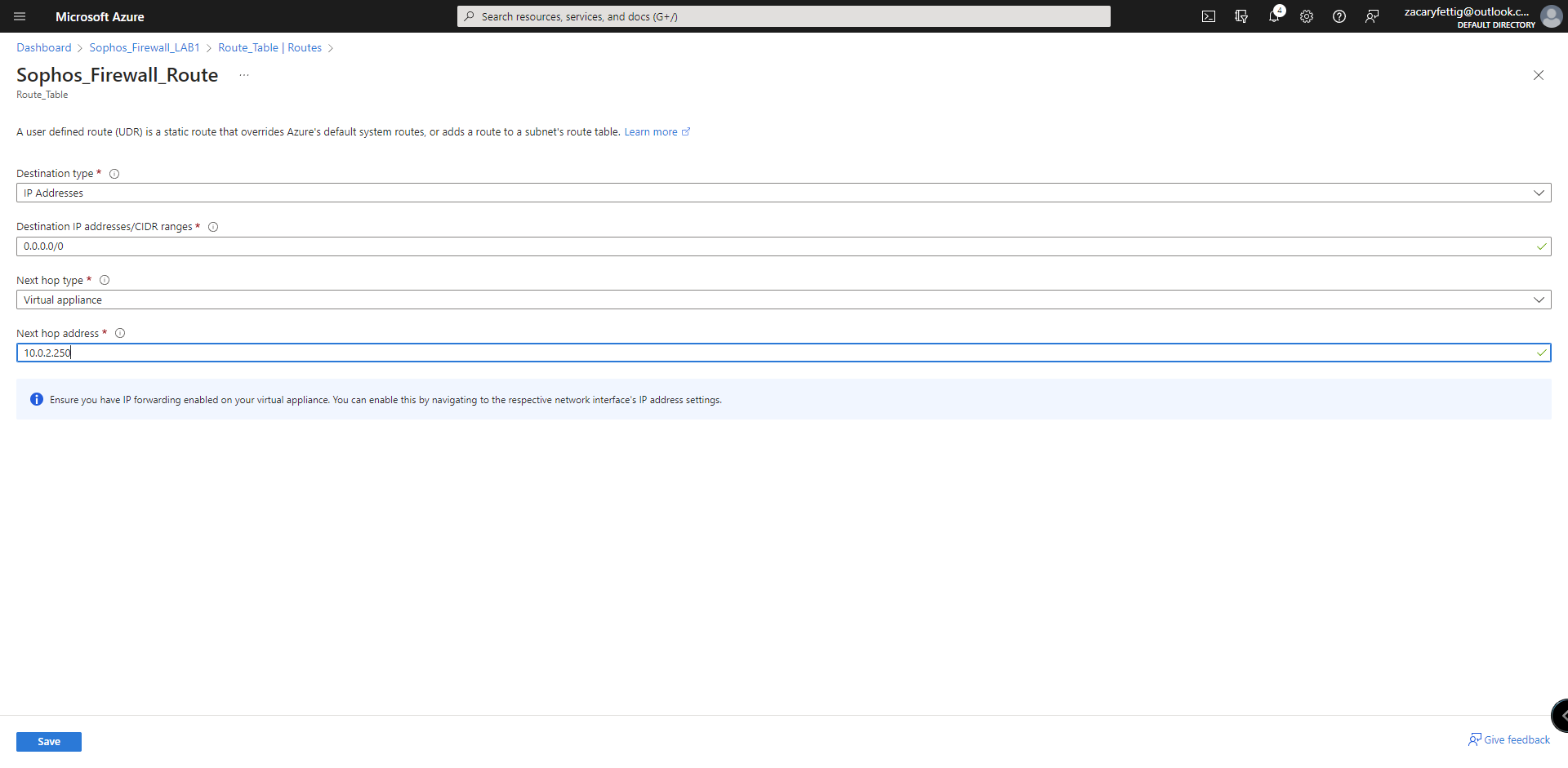
4. Add a static route to each firewall to allow the XG to see the subnet.