This project goes over: creating an Azure File Share, connecting to the Azure File Share, Syncing Azure Files to/from a Windows Server based file share, private VNet and on-prem access to file share, integrating on-prem Active Directoy Authentication into an Azure File Share.
Azure Files Migration
- Home
- Portfolio

Zacary Fettig
-
Pine Cove Consulting MSP
-
Azure Solutions Architect Expert | MCSE: Core Infrastructure
Azure Files Migration
Azure File Sync
1. Create an Azure Storage Account

2. Add Azure file Share from within the Storage Account. Select Storage Tier based on file share use case.

3. Create a new Azure File Sync Resource. Select Subscription, Resource Group, Name the Storage Sync Service, Select Region. On the networking tab, select your preference in network connectivity.



4. Next we will add in a server into the Sync. Go to the Registered Servers tab in the new FileSync resource. Select Download Azure File Sync agent.
5. On the download webpage select download and download the right package for your Operating System.

6. Launch the StorageSyncAgent installer. Select next on the first page.
7. Accept the End-User Agreement
8. Configure Proxy Settings based on your environment. Leave as default in the case of no proxy server.
9. Leave as default and select next.
10. Select Install and finish once install has completed.

11. Window will pop up to check that the most up to date version is installed. Select OK once finished.
12. The next window asks you to select the Azure Environment type and select sign in.
13. Select your subscription, Resource Group, and the already created Storage Sync Service.
14. Once Registration competes, select close to finish the wizard.
15. Registered Server will now show in Azure.
Create a Sync Group
1. Select Sync Groups tab in the File Sync resoure and select add Sync Group
2. Select Sync group name, subscription, Storage Account and the File Share.
3. Once created, click on the File Share Sync Group to open it.
4. Select add Server endpoint and select the server and the path on that server to the file share data.
5. Cloud Tiering will allow settings set to only store data locally based on certain defined policies. For example Storing Hot data in both locations, but not syncing cold data or choosing to sync based on a last accessed date.
6. Intial Upload settings configures to merge or overwrite all existing files in the Azure File share. Initial Download will specify whether All File content will be downloaded automatically. Avoid tiered files download option will only show files once the files/folders are fully downloaded.
7. Once created, The Server Endpoint will show up in the list and start syncing. Select the server to view more details.
8. Once fully synced, Upload to cloud and Download to Server will show green check marks. Files from the server be seen in the Azure File share. The process for Azure File Sync is complete.

Connecting to The File Share as a network drive.
1. Select connect from the top menu and select the Storage Account Key box. 
2. Run the the script to connect the file share.
Note: If port 445 is blocked by the ISP, the share will not connect. In this case Express Route or a VPN will be needed to connect the File Share.
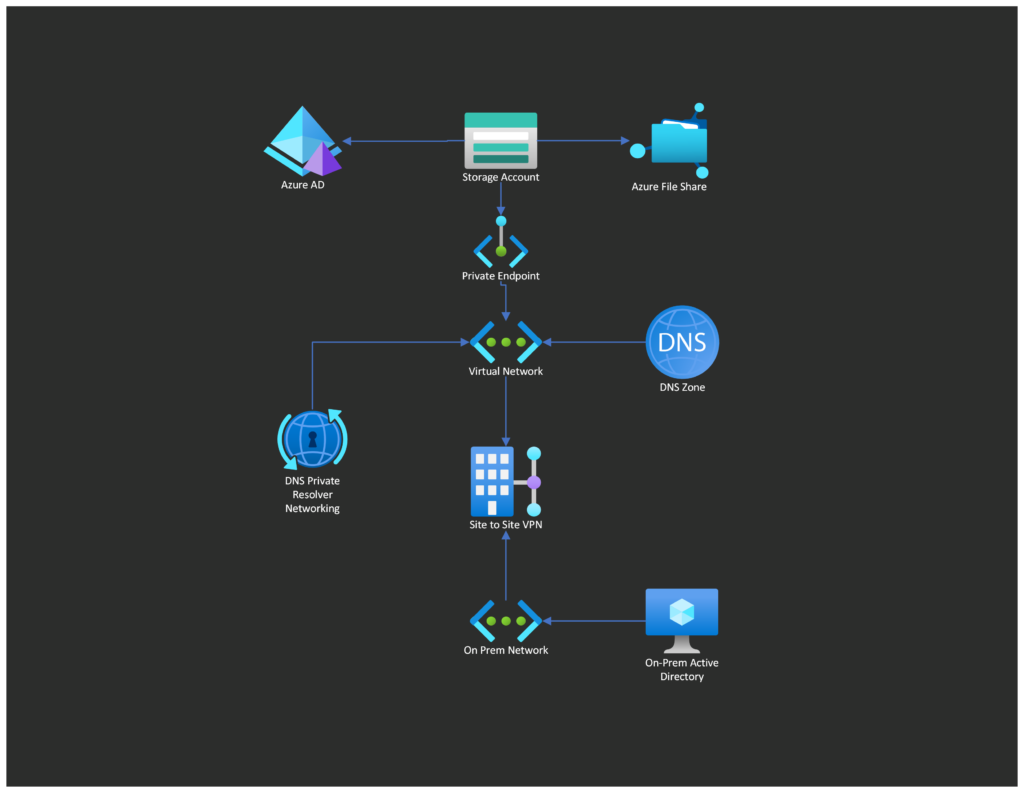
Private VNet access to file Share in Azure and connecting private IP/DNS to on-prem environments.
Create a Private Endpoint so that the storage account can privately connect to an internal virtual network.
1. Within the storage account, select the networking tab. Select the private endpoint tab and add a new private endpoint.
2. Select Subscription, resource group, name the private endpoint, and select the region.
3. Select file as the target sub-resource
4. Select virtual network and subnet. Select statically allocate IP to define your own IP or dynamically allocate IP for a randomly selected IP in the subnet.
5. Leave DNS option as default. Finish wizard selecting review + create.
6. The newly created endpoint will show up in the list. Select the endpoint to view the private IP information.
Create a new dns zone to resolve core.windows.net to the private IP of the storage account.
1. Select subscription and resource group. Name of the zone will be: file.core.windows.net
2. Connect the dns zone to your vnet to activate the zone.
3. Create an a record using the name of the storage account as the name and the IP pointing towards the private IP of the storage account. After the a record is set, the storage account will now resolve to the private IP address within that Azure VNet.
Resolving the private DNS/IP on an on-prem network
prerequisites: VPN/Express Route Connection from Azure to on-prem network.
1. Create a private dns resolver resource in Azure. Select subscription and resource group. Give the private resolver a name. Select region and virtual network. Select next.
2. Create an inbound endpoint within the private resolver wizard. Name the endpoint and create new subnet that will act as the landing point into Azure for the resolver. Select desired IP address assignment type. Dynamic for a random IP within the subnet chosen or Static to specify your own. Select review and create.
3. Once created, click on the inbound endpoints tab within the private resolver resource. Note the private IP address, as the IP will be needed in the next step.
4. A Conditional Forwarder will forward the traffic to the inbound endpoint which will be able to resolve Azure DNS. On the on-prem Windows DNS Server create a conditional forwarder with the domain of <yourStorageAccount>.file.core.windows.net. in the IP section add the IP from the previous step.
5. Nslookup will show <yourStorageAccount>.file.core.windows.net will now resolve to the private IP address of the Azure File Share.
Integrating on-prem Active Directory authentication into an Azure File Share
Prerequisites: Storage Account will need line of sight to domain controller. This will need to be done either through public access on a non ISP blocked port 445 connection, VPN, or Express Route. AD Connect will also need to be setup for this to work.
1. Download the AzFilesHybrid powershell module. The module will be used to run the necessary powershell commands to connect the storage account to AD.
2. Unzip the folder. In powershell, change directory directory inside the folder. Run the command .\CopytoPSPath.ps1
3. Run the command: Import-Module -Name AzFilesHybrid -Verbose
4. Run the command: Import-Module -Name AzFilesHybrid
5. The command in the steps below will generate a computer object to communicate with Azure Files. Create an OU that does not have any password policies assigned to it for the computer object.
6. join Azure file share to on-prem domain.
command: Join-AzStorageAccount -ResourceGroupName "rg2" -StorageAccountName "yourStorageAccountName" -OrganizationalUnitDistinguishedName "OU=yourOU",DC=yourADDomain, DC=com"
7. Computer object will appear in AD in the specified OU.
Assign permissions to file share
1. In Active Directory create a new group for AzureFilesReader, AzureFilesContributor, and AzureFilesReader. These group will correspond to the rbac permissions that will be set on the Azure File Share. AD users will need to be added to these groups for file share access.
2. Assign RBAC Permissions. On the IAM tab of the file share resource select the add button. Select new role assignment. Assign each group replicated over using AD connect to the corresponding RBAC permissions in Azure.

3. Connect to the storage account using the storage account key
command: net use z: \\<storageAccountName>.core.windows.net\<fileShareName> <storageAccountKey> /user:Azure\storageAccountName
4. After running the command, the Azure Files will map the drive. Right click the drive and select properties. Click on the security tab and select edit. Add in each group that was created in AD with the permissions below. This will set the permissions that each group will have on the File Share.

- Azure Files Reader: Read, read & Execute, List Folder Contents
- Azure Files Contributor: Modify, Read & Execute List Folder Contents, Read, Write
- Elevated Contributor: Full Control
5. Assign AD users to groups based on the permissions that they need on the share. Mount network drive using Active Directory credentials. Once the drive is connected, the setup is complete.
6. To rotate the keys or in case of a password expiration in AD, use the following command
command: Update-AzStorageAccountADObjectPassword -RotateToKerbKey Kerb1 -ResourceGroupName $ResourceGroupName -StorageAccountName $StorageAccountName
Use name of previous file share with Azure Files
If you are looking for a solution to name the mounted share the same as a previous on-prem file share, Microsoft has released a great video that shows how to do this using DFS Namespaces. To accomplish this you will still need a Windows based server with DFS-N installed.
With the steps followed in this document, DFS can be setup on an existing on-premis domain controller to save costs, since we have used a private resolver for the forwarding of DNS traffic. Setting up DFS-N starts at the 9:30 minute marker in the video.
Microsoft DFS-N Configuration: https://www.youtube.com/watch?v=a-Twfus0HWE&t=608s



